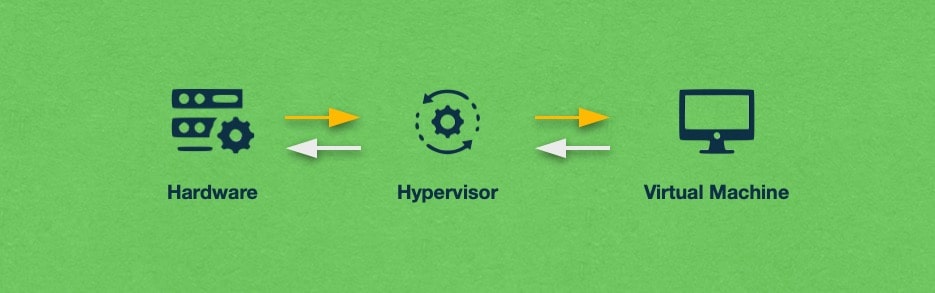
A hypervisor is a special piece of software that can be installed on most modern-day computers. The hypervisor’s function is to act as the foundation on top of which you can install full-fledged operating systems like Windows, Linux, macOS, and others. When installed, these operating systems interact only with the hypervisor itself and have no knowledge of your actual computer hardware. Due to this reason, such installations are commonly referred to as virtual machines (VMs), and the hypervisor is regarded as the virtual machine monitor (VMM).
In essence, the hypervisor abstracts the operating system of the virtual machine from the underlying server hardware and acts as the intermediary layer between them. So when a program in the virtual machine needs to process some data, it sends the processing request to the hypervisor. The hypervisor then passes this request along to the computer hardware.
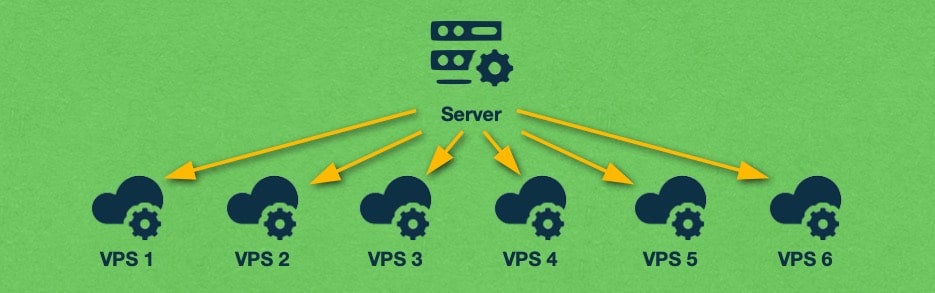
The great thing about the hypervisor is that it can create and manage multiple virtual machines at the same time. In fact, on powerful systems, the hypervisor can seamlessly interact with dozens of virtual machines at once. Each virtual machine operates independently and has no knowledge of other virtual machines that may be running. By using multiple virtual machines on a single server, companies are able to fully utilize the computer’s available resources like CPU, RAM, and network bandwidth.
The physical computer that powers the virtual machines is often referred to as a host, while each virtual machine is known as a guest.
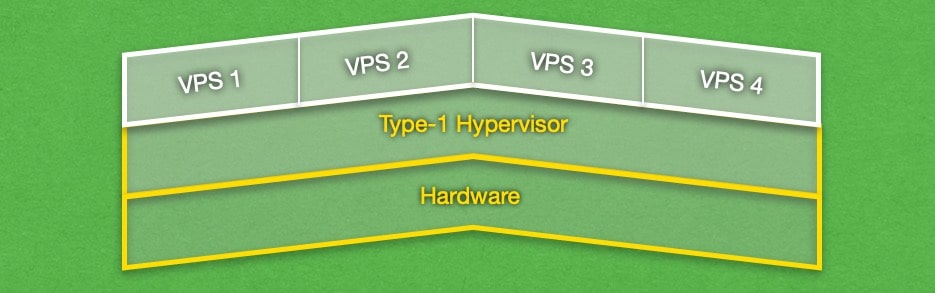
There are two types of hypervisors: Type-1 and Type-2. Type-1 hypervisors run directly on the hardware and either act as the operating system or are embedded straight into the computer’s firmware. Type-1 hypervisors are regarded as more secure and offer good performance, but they are difficult to set up.
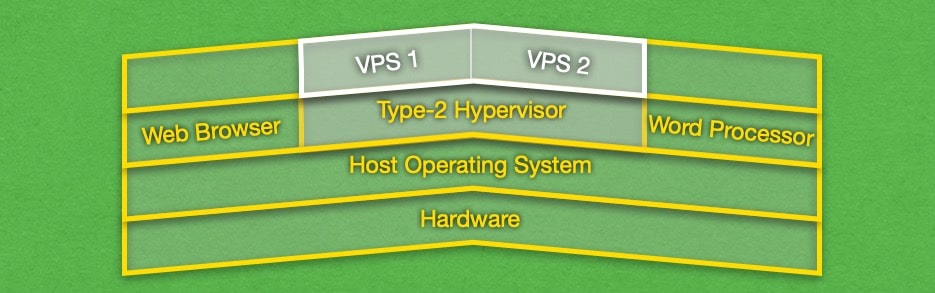
Type-2 hypervisors, on the other hand, are installed on top of a regular operating system and take the form of just another program that you can interact with. The setup process for Type-2 hypervisors is significantly simpler, but you will not get optimal performance and your level of protection will not be as high as with a Type-1 hypervisor.
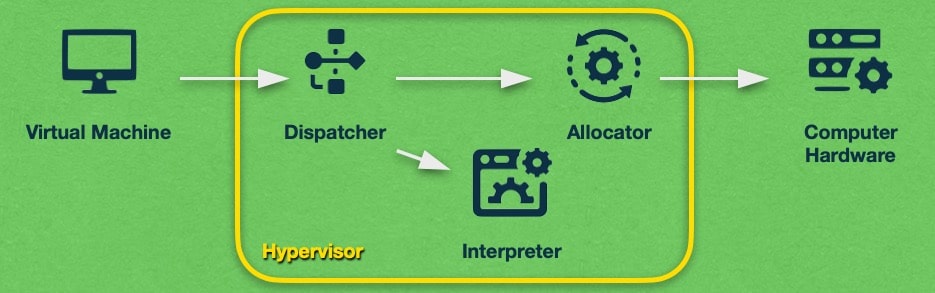
Regardless of its type, each hypervisor is comprised of three basic components: a dispatcher, an allocator, and an interpreter. When these three components are working in concert, they are able to emulate a system’s hardware, thus allowing you to run virtual machines.
The dispatcher is the component that receives the instructions sent from the virtual machine. It does not carry out these instructions, but instead, it just forwards them to one of the other two modules.
The allocator manages the number of system resources that are available to the virtual machine. If instruction would require a change in the virtual machine’s current resource allocation, then the allocator will be invoked to carry out that change.
Lastly, the interpreter is a collection of interpreter routines. These routines are executed every time the virtual machine tries to execute a privileged instruction. Each routine acts as a trap and when the privileged instruction activates a trap, the corresponding routine is executed.
To learn even more about what a hypervisor is, how it is used to control your VPS, and what types of hypervisors there are, continue reading or jump to the section that interests you:
Advantages
Hypervisors, and the virtual machines that are powered through them, come with many advantages that are not found in conventional computers. Below, we will list some of the more notable ones:
- The hypervisor is capable of running multiple virtual machines at the same time. Doing so allows you to not only do more work but also fully utilize the computer hardware that is available to you.
- All virtual machines are completely isolated from one another. Virtual machines do not know whether they are sharing the computer hardware with other VMs. What is more, they are not even aware that they are virtual in nature and are not hardware-based computers.
- Thanks to its VM isolation capabilities, the hypervisor can offer a high degree of stability. Even if a virtual machine crashes, it won’t affect the stability of the other VMs or the underlying computer hardware.
- Since virtual machines are completely virtual, they are not tied to any specific computer hardware. Instead, they are tied only to the hypervisor. And thanks to this hardware platform independence, VMs can be easily migrated from one computer system to another.
- The hypervisor also enables very fast deployment for new VMs. Since the VM is just software, it can be up and running within minutes. In contrast, purchasing, transporting, and assembling a new hardware computer can take hours, days, or even weeks.
- Lastly, the hypervisor provides flexible hardware specifications for virtual machines. You can easily add more computing resources when the need arises and scale back when things settle down.
Disadvantages
While the hypervisor comes with many great benefits, it is not the ideal solution in every scenario. Below, we will list some drawbacks that you should keep in mind:
- Running five virtual machines means that there are five full-featured operating systems running on your hardware. And chances are that the VMs do not utilize every single aspect of the OS that powers them. As a result, the hypervisor and VMs, in general, waste computing resources to power OS features that are never used. The wasteful nature of the hypervisor is exacerbated when you compare VMs to containers. A container packages just the application you wish to run along with a portion of the operating system that contains just the necessary services and frameworks.
- When run in a commercial setting, a single physical server may be used to power multiple virtual machines belonging to different clients. If one of those VMs is put under a heavy load, it can consume a lot of server resources, thus affecting the performance of the other virtual machines. Such VMs are often referred to as noisy neighbors. Fortunately, most hosting providers will configure the hypervisor to limit the number of computing resources each virtual machine can utilize, thus mitigating the issue to a large extent.
- Lastly, at the end of the day, the hypervisor is still just a software product and as such, it is vulnerable to attacks. Should an attacker gain control over the hypervisor, this can cause serious security issues. If this happens, the attacker will be able to monitor all activities that are performed in each VM under the hypervisor’s control. To make matters worse, antivirus software running on virtual machines will provide no indication of a security issue since the attack has taken place on a software layer underneath the VM operating system.
What Does a Hypervisor Do?
The hypervisor is the middle layer that stands between a computer’s hardware and the virtual machines that run on top of it. The hypervisor’s two main tasks are to create virtual machines and to dynamically allocate computing resources to existing VMs according to their needs.
Hypervisors may have complete or partial control over the hardware system’s computing resources like CPU, RAM, hard drives, and bandwidth. Type-1 hypervisors typically pool all available computing resources together and assign them to VMs as needed. Type-2 hypervisors, on the other hand, can manage only a portion of the available hardware resources.
When a virtual machine is presented with computing resources from the hypervisor, it thinks that these resources are actual computer hardware that is solely under its control. This is true regardless of the operating system that the virtual machine may be running. Speaking of operating systems, virtual machines are able to run all modern OSes such as Windows, Linux, macOS, and other Unix-like operating systems.
It is precisely the ability to manage operating systems where the hypervisor gets its name. The term hypervisor is derived from the term supervisor which historically has been used to describe the kernel of an operating system. The hypervisor acts as the supervisor of the other supervisors, hence the name hypervisor (hyper being a stronger variant of super).
One of the most important features of a hypervisor is its ability to run multiple virtual machines at the same time. This allows companies to fully utilize all available hardware resources and consolidate multiple systems into one physical package.
To make sure that each virtual machine is performing optimally, the hypervisor needs to run each VM in complete isolation from the other VMs as well as the underlying hardware. Doing so introduces a high degree of fault tolerance where a virtual machine crash will not bring down other virtual machines or the entire physical computer. In addition to isolation, the hypervisor also needs to carefully triage the instructions sent by each VM so one virtual machine does not accidentally access the information of another VM.
The ability to seamlessly run multiple virtual machines from a single physical computer at the same time forms the basis of cloud hosting. Without the hypervisor and virtual machines by extension, we would not have this new innovative hosting solution that is rock-solid in terms of uptime and infinitely scalable in terms of computing resources.
Hypervisors are similar to containers in many ways, however, they differ in their scope. Hypervisors isolate entire operating systems while containers have a narrower scope and only isolate the target application as well as any services and frameworks that are necessary for the application to run properly. You can read our article on containers to get a better idea of what they are, or you can learn the differences between the two by checking our comparison between hypervisors and containers
How Does a Hypervisor Control My Virtual Private Server?
A Virtual Private Server (VPS) is just a virtual machine that is used for web hosting purposes. As such, it is also governed by a hypervisor. The hypervisor enables three unique features that make virtual private servers an excellent hosting solution. In the next few sections, we will take a closer at these three features, starting with isolation.
Isolation
Isolation refers to the fact that each VPS is completely standalone and independent from all other virtual servers that may be running on the platform. In other words, if you want to reboot your VPS, you may do so without affecting any other VMs or the computer hardware that is powering your virtual server. Similarly, if one VPS is compromised or freezes, the hypervisor keeps this event isolated to that VPS only without affecting the rest of the network. This makes VPS hosting one of the most stable Internet hosting packages out there.
What is more, isolation is also used when it comes to the amount of processing power each VPS is allowed to use. Here at AwardSpace, we place caps on each of our VPS hosting packages. These caps ensure that each VPS package comes with a predetermined amount of processing power, RAM, storage, and bandwidth. These server resources are dedicated to your VPS only and cannot be used by third parties. As a result, you are provided with a dependable and stable hosting experience that stands in stark contrast to the regular shared hosting model.
Mobility
Thanks to the hypervisor, virtual servers benefit from increased mobility. Since a VPS is purely virtual in nature, the entire system can be seamlessly moved from one physical computer to another. In fact, the migration can occur with zero disruptions to the VPS operation and in a relatively short amount of time. Such VPS transfers are often referred to as live migrations. Live migrations are possible because virtual machines are completely decoupled from the hardware that powers them.
Live migration is taken a step even further with the use of management software that monitors the health of the physical servers. Should a server begin to fail, the management software can automatically move all virtual servers from the failing machine to backup computing hardware. Such systems can ensure near-100% VPS uptime with seamless migration that is completely transparent for the VPS owner.
Snapshots
Snapshots are another very handy feature that allows you to create a restore point for your VPS. The great thing about snapshots is that they are taken while the VPS is still running. There is no need to power it down or disrupt the applications on it in any way.
This is possible since the hypervisor has complete access to the virtual machine’s disk storage in addition to its operating memory (RAM). So a snapshot will not only save your files, but it will also save all of your open applications and the exact state that they are in. As such, restoring from a snapshot of a virtual machine that is in operation will provide you with a VPS that is powered on with your applications already running.
Here at AwardSpace, we take full advantage of this snapshot functionality. We allow you to take a snapshot of your VPS at any time with a single click from our Server Control Panel. To take full advantage of this great feature, sign up for one of our VPS plans.
What Types of Hypervisors Are There?
There are two distinct hypervisor types: Type-1 and Type-2. Both types of hypervisors are similar in that they allow you to run multiple virtual servers from a single physical computer and each VM can use a different operating system. That said, there are some notable differences between the two. Below, we will examine each hypervisor type in greater detail.
Type-1 Hypervisors
Type-1 hypervisors are often referred to as native or bare-metal hypervisors since they run directly on top of a physical computer’s hardware. You can think of Type-1 hypervisors as super-specialized operating systems since they interact directly with the system components. Moreover, when you use a Type-1 hypervisor, you can use the physical server to run virtual machines only. This is because Type-1 hypervisors are not general-purpose operating systems where you can install additional applications like a web browser, for example.
When you launch a Type-1 hypervisor, you will notice that its interface is very basic. In most cases, you get just a command line with just a few options that you can configure. The actual VPS deployment and administration happens on a separate computer that is running a remote management console.
The Type-1 hypervisor is kept bare-bones intentionally. On one hand, the fewer extraneous features mean a higher degree of performance. On the other, having fewer features means that there are fewer attack vectors for hackers. This is the reason why Type-1 hypervisors are regarded as fairly secure pieces of technology.
Speaking of performance, Type-1 hypervisors boast better overall speeds when compared to Type-2 hypervisors. The main reason for this advantage is that the hypervisor interacts with the server hardware directly. Moreover, you are allowed to allocate all available hardware resources to virtual machines since computers running Type-1 hypervisors do not have conventional operating systems installed.
When it comes to resource allocation, you are allowed to change the number of available computing resources for a VPS at any time and without having to power down or reboot the VPS. In addition, Type-1 hypervisors allow you to over-allocate system resources. In other words, you can give your virtual servers more computing power than what is physically available on the server.
For example, if the server has 64GB of RAM, you can have three virtual private servers each using 24GB of RAM. You would have allocated 72GB of RAM when in reality the server has only 64GB. The reason why this is possible is that the hypervisor does not reserve the allocated memory. Instead, all virtual machines draw computing power from the same pool of hardware resources.
The thinking in our example scenario is that the three virtual servers would never utilize all of their allowed RAM at the same time. As such, the three virtual private servers can coexist by drawing from a pool of 64GB of RAM in total. And should the average load for each VPS increase with time, the hypervisor can be used to seamlessly transition one of the virtual servers onto new hardware.
Type-1 hypervisors are most often used in large enterprises, web hosting, and cloud computing. Popular Type-1 hypervisors include Microsoft Hyper-V, KVM, Xen, VMware vSphere, and others.
Type-2 Hypervisors
Type-2 hypervisors, often called hosted hypervisors are software products that run on top of a conventional operating system. The hypervisor takes the form of a system process that sits on the same level as other application processes, such as your web browser or a word processor.
The addition of a host operating system is the key difference between the Type-2 hypervisor when compared to its Type-1 counterpart. The host OS acts as an additional layer in the communication path between the virtual machine and the server hardware. For example, if a VM wants to execute certain instructions, it passes them along to the Type-2 hypervisor. The hypervisor, in turn, passes the instructions to the host operating system. It is then up to the host operating system to pass these instructions to the computer hardware for execution.
Despite the Type-2 hypervisor existing within a host operating system, it can still be used to run other operating systems. For example, you can use a Type-2 hypervisor on a Windows PC to run a Linux virtual machine. Or you can use a Mac and interact with a Windows VM.
As we have outlined earlier, Type-2 hypervisors do not run directly on the system hardware. Instead, they need to go through the host operating system for every operation that the virtual machine executes. This results in unnecessary overhead which negatively impacts performance. As such, a virtual machine powered by a Type-2 hypervisor will be noticeably slower than the same VM powered by a Type-1 hypervisor.
What is more, whatever system resources you allocate to a VM will be reserved immediately if the virtual machine is powered by a Type-2 hypervisor. For example, if your computer has 16GB of RAM and you create a virtual machine with 6GB of RAM, then these 6 GB of RAM will be reserved even if they are not fully utilized. As a result, the host OS will have only 10GB of RAM available.
While a Type-1 hypervisor allows over-allocating system resources, Type-2 hypervisors are not able to do that. To make things worse, the closer you get to allocate all of your available hardware resources to VMs, the higher risk you run of crashing the host operating system.
At this point, you may be thinking why would someone opt to use a Type-2 hypervisor when it clearly offers worse performance when compared to the Type-1 variant. The answer is that Type-2 hypervisors are extremely easy to set up and use. Unlike a Type-1 hypervisor, Type-2 comes packaged as an application for your computer. The application is installed like any other and it contains both the hypervisor itself as well as the management software where you can create, edit, boot up, power down, and remove virtual machines.
When you use a virtual machine powered by a Type-2 hypervisor, the VM will have its own window. You can then interact with the virtual machine just like any application that you have installed on your PC.
Due to their ease of use, Type-2 hypervisors are often utilized in software testing and development. Also, regular users can take advantage of virtualization to try out new operating systems or run applications that are not compatible with their host operating system. Some of the most popular Type-2 hypervisors include VMware Fusion Player, VMware Player, Oracle VirtualBox, Parallels Desktop, and VMware Workstation.
Conclusion
Thanks to the incredible advancements in computing hardware in the last decade or so, virtual machines, and hypervisors by extension, have become an integral part of many organizations’ workflows. Whether it is powering mission-critical systems or performing software tests, VMs have earned their place in the IT world. And when you consider that the cloud is powered exclusively by VMs, it is clear that the hypervisor and virtual machines are here to stay.
